Deny Users Access to PC Settings and Control Panel using Group Policy
In a domain-joined networked environment, we always need to restrict users’ access to most PC settings and resources. It is necessary to do so for security and safety reasons. One crucial restriction that we always need to apply is to deny users access to PC Settings and Control Panel. And that is what this article is about. More specifically, this article covers the detailed steps to preventing users’ access to the Control Panel and PC Settings using Group Policy on Windows Server 2022.
In our example, our domain controller machine runs Windows Server 2022, on which we create the group policy. We create an Organization Unit (OU) level group policy directly on the (OU) that contains the users to which we apply the policy.
You may also like to read Install Active Directory On Windows Server 2022 Using PowerShell.
Steps to Deny Access to PC Settings and Control Panel
As we described in the scenario earlier, we create the policy that is linked to an OU, which contains the users to which we apply the restriction. We can create the group policy first and link that to the OU, or we can create the group policy directly on the OU. Either way ends up with the same result. However, we go with the second approach in our example. That being said, let’s go with the steps.
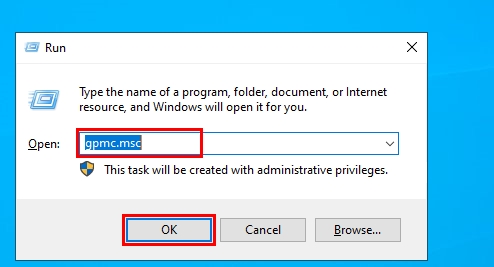
- Press down the Windows key + R keys on your keyboard to open the Run dialogue box.
- Type in
gpmc.mscand press Enter to open the Group Policy Management console.
- Right-click on the OU to which you want to associate the group policy. Then, select Create a GPO in this domain,… option.
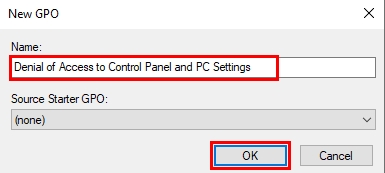
- Put a name for the Group Policy Object (GPO) in the relevant box, and click OK.
- Once the GPO is created, right-click on it, and select Edit from the context menu.
- On the Group Policy Management Editor window, expand Policies under User Configuration. Then, expand the Administrative Template and click on Control Panel. Finally, double-click on Prohibit access to Control Panel and PC settings.
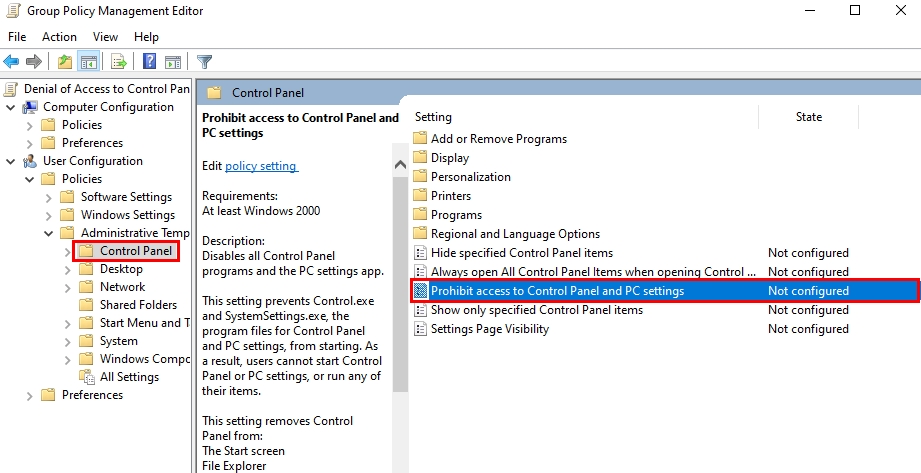
- On the configuration window, check the Enabled option. Then, click OK, and close the Group Policy Management Editor window.
To this end, we have created the group policy to prevent users’ access to the Control Panel and PC settings. We created it directly linked to the OU that contains user accounts that we want to restrict. So, it is all done. To verify it, go with the next section.
Verifying the Above Group Policy Configuration
To check the above restriction, we need to log in with a user account that is a member of the OU to which we linked the group policy. Then, we update the group policy and try to open the Control Panel and PC Settings. See the below steps.
- Login to the client’s computer with a user account that is a member of the OU to which you linked the restriction.
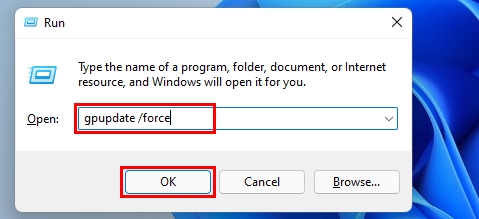
- Run
gpupdate /forcein the Run dialog box to perform group policy updates. Wait for a while until the group policy completes.
- Once the group policy gets updated, try to open the Control Panel or PC Settings. It doesn’t open, and you will face the pop-up window shown in the below pic.
That is all we need to do to check how the restriction we configured works and if it is applied correctly.
Conclusion
It is a common setting in a domain environment to deny users access to the Control Panel and PC settings. It is essential for security and safety reasons. As the steps discussed above, we can apply this restriction simply by defining and configuring a group policy object to an OU that contains the target users.
In the end, I hope you found this article helpful. Do not hesitate to share your thoughts and queries in the comment section.
