How to Configure Switch Port Security on Cisco Switches?
Configuring Port Security on Catalyst 4500 Series Switch Cisco IOS Software Configuration Guide
This article describes how to configure switch port security on Cisco Switches. It provides guidelines, procedures, and configuration examples. To practice and learn to configure port security on Cisco switch, just download the port security packet tracer lab or create your own lab and follow the switch port security configuration guideline.
Download Switch Port Security Configuration Packet Tracer Lab.
Port Security Guidelines and Restrictions
Follow these guidelines when configuring port security.
- A secure port cannot be a trunk port.
- A secure port cannot be a destination port for Switch Port Analyzer (SPAN).
- A secure port cannot belong to an EtherCha
![]() nnel port-channel interface.
nnel port-channel interface. - A secure port and static MAC address configuration are mutually exclusive.
Configure Switch Port Security
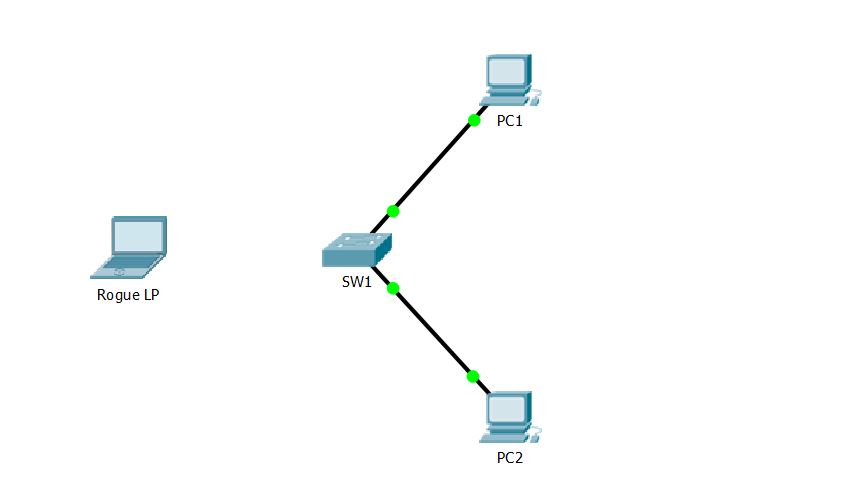
These sections describe how to configure port security using the Packet Tracer – Configuring Switch Port Security Lab.
In this activity, you will configure and verify port security on a switch. Port security allows you to restrict a port’s ingress traffic by limiting the MAC addresses that are allowed to send traffic to the port.
Part 1: Configure Port Security
a. Access the command line for S1 and enable port security on Fast Ethernet ports 0/1 and 0/2.
SW1>enable SW1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. SW1(config)#interface range fastEthernet 0/1-2 SW1(config-if-range)#switchport mode access SW1(config-if-range)# SW1(config-if-range)#switchport port-security SW1(config-if-range)#
b. Set the maximum so that only one device can access the Fast Ethernet ports 0/1 and 0/2.
SW1(config-if-range)#switchport port-security maximum 1 SW1(config-if-range)#
c. Secure the ports so that the MAC address of a device is dynamically learned and added to the running configuration.
SW1(config-if-range)#switchport port-security mac-address sticky SW1(config-if-range)#
d. Set the violation so that the Fast Ethernet ports 0/1 and 0/2 are not disabled when a violation occurs, but packets are dropped from an unknown source.
SW1(config-if-range)#switchport port-security violation restrict SW1(config-if-range)#
e. Disable all the remaining unused ports. Hint: Use the range keyword to apply this configuration to all the ports simultaneously.
SW1(config)#interface range fastEthernet 0/3-24, gigabitEthernet 0/1-2 SW1(config-if-range)#shutdown
It’s all and enough to configure switch port security on this lab. Let’s test it.
Part 2: Verify Port Security
Try to test your switch port security configuration with ping command and testing with the rogue laptop on the lab
- a. From PC1, ping PC2.
- b. Verify port security is enabled and the MAC addresses of PC1 and PC2 were added to the running configuration with “show run” command.
- c. Attach Rogue Laptop to any unused switch port and notice that the link lights are red.
- d. Enable the port and verify that Rogue Laptop can ping PC1 and PC2. After verification shut down the port connected to Rogue Laptop.
- e. Disconnect PC2 and connect Rogue Laptop to PC2’s port. Verify that Rogue Laptop is unable to ping PC1.
- f. Display the port security violations for the port Rogue Laptop is connected to.
- g. Disconnect Rouge Laptop and reconnect PC2. Verify PC2 can ping PC1.
- h. Why is PC2 able to ping PC1, but the Rouge Laptop is not?
That’s all, you need to learn about to configure switch port security on Cisco switches. If you need to study more about switch port security, try to read a book or simply read the below materials.
Default Port Security Configuration
| | |
|---|---|
| Port security | Disabled on a port |
| Maximum number of secure MAC addresses | 1 |
| Violation mode | Shutdown. The port shuts down when the maximum number of secure MAC addresses is exceeded, and an SNMP trap notification is sent. |
| Aging | Disabled |
| Aging type | Absolute |
| Static Aging | Disabled |
| Sticky | Disabled |
Overview of Configure Switch Port Security
You can configure MAC addresses to be sticky. These can be dynamically learned or manually configured, stored in the address table, and added to the running configuration. If these addresses are saved in the configuration file, the interface does not need to dynamically relearn them when the switch restarts. Although sticky secure addresses can be manually configured, it is not recommended.
You can configure an interface to convert the dynamic MAC addresses to sticky secure MAC addresses and to add them to the running configuration by enabling sticky learning. To enable sticky learning, enter the switchport port-security mac-address sticky command. When you enter this command, the interface converts all the dynamic secure MAC addresses, including those that were dynamically learned before sticky learning was enabled, to sticky secure MAC addresses.
The sticky secure MAC addresses do not automatically become part of the configuration file, which is the startup configuration used each time the switch restarts. If you save the sticky secure MAC addresses in the configuration file, when the switch restarts, the interface does not need to relearn these addresses. If you do not save the configuration, they are lost
If sticky learning is disabled, the sticky secure MAC addresses are converted to dynamic secure addresses and are removed from the running configuration.
After the maximum number of secure MAC addresses is configured, they are stored in an address table. To ensure that an attached device has the full bandwidth of the port, configure the MAC address of the attached device and set the maximum number of addresses to one, which is the default.
A security violation occurs if the maximum number of secure MAC addresses has been added to the address table and a workstation whose MAC address is not in the address table attempts to access the interface.
You can configure the interface for one of these violation modes, based on the action to be taken if a violation occurs:
- Restrict—A port security violation restricts data, causes the SecurityViolation counter to increment, and causes an SNMP Notification to be generated. The rate at which SNMP traps are generated can be controlled by the SNMP-server enable traps port-security trap-rate command. The default value (“0”) causes an SNMP trap to be generated for every security violation.
- Shutdown—A port security violation causes the interface to shut down immediately. When a secure port is in the error-disabled state, you can bring it out of this state by entering the errdisable recovery cause psecure-violation global configuration command or you can manually re-enable it by entering the shutdown and no shutdown interface configuration commands. This is the default mode.
You can also customize the time to recover from the specified error-disable cause (default is 300 seconds) by entering the errdisable recovery interval command.
Source: Cisco
Related Search Queries:
- Cisco port security violation
- Switchport port-security maximum 2
- Cisco port security violation options
- Switchport port-security violation restrict vs protect
- Port security configuration in packet tracer
- Switchport port-security mac-address sticky
- Port security in networking
- Port security pdf
- Switchport port-security maximum
- Switchport port-security violation restrict vs protect
- Cisco port security violation options
- Switchport port-security mac-address sticky

Thanks for the information shared! It was great!!