CCNA Security Chapter 3 Exam Questions With Answers – Updated
Updated CCNA Security Exam Questions and Answers. CCNA Security Chapter 3 Exam Answers
Looking for CCNA Security Exam Answers? Here you can test and review all updated CCNA Security Chapter 3 exam questions and answers. It is just for educational purposes.
These questions are the latest CCNA security chapter 3 exam questions with answers. Please share the new questions through the comment section. We will reply it with the correct answer.
CCNA Security Chapter 3 Exam Questions and Answers
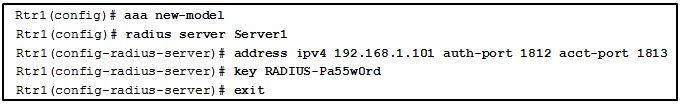
1: Refer to the exhibit. Which statement describes the configuration of the ports for Server1?
The configuration is using the default ports for a Cisco router.
The configuration will not be active until it is saved and Rtr1 is rebooted.
The configuration of the ports requires 1812 be used for the authentication and the authorization ports.
The ports configured for Server1 on the router must be identical to those configured on the RADIUS server.
SSH
RADIUS
TACACS+
ACS
The local username database will provide a backup for authentication in the event the ACS servers become unreachable.
A local username database is required when configuring authentication using ACS servers.
Because ACS servers only support remote user access, local users can only authenticate using a local username database.
Without a local username database, the router will require successful authentication with each ACS server.
debug tacacs accounting
debug aaa authentication
debug tacacs events
debug tacacs
Windows Server only supports AAA using TACACS.
Windows Server uses its own Active Directory (AD) controller for authentication and authorization.
Windows Server cannot be used as an AAA server.
Windows Server requires more Cisco IOS commands to configure.
MD5
RADIUS
SSH
TACACS+
Implement Cisco Secure Access Control System (ACS) only.
RADIUS and TACACS+ servers cannot be supported by a single solution.
Implement both a local database and Cisco Secure Access Control System (ACS).
Implement a local database.
TACACS+ is backward compatible with TACACS and XTACACS.
TACACS+ uses UDP port 1645 or 1812 for authentication, and UDP port 1646 or 1813 for accounting.
TACACS+ provides authorization of router commands on a per-user or per-group basis.
TACACS+ is an open IETF standard.
accessibility
authorization
authentication
auditing
accounting
The login succeeds, even if all methods return an error.
It uses the enable password for authentication.
It accepts a locally configured username, regardless of case.
It defaults to the vty line password for authentication.
It uses less network bandwidth.
It requires a login and password combination on the console, vty lines, and aux ports.
It provides a fallback authentication method if the administrator forgets the username or password.
It specifies a different password for each line or port.
accounting
accessibility
authentication
authorization
Accounting can only be enabled for network connections.
Users are not required to be authenticated before AAA accounting logs their activities on the network.
Accounting is concerned with allowing and disallowing authenticated users access to certain areas and programs on the network.
Possible triggers for the aaa accounting exec default command include start-stop and stop-only.
Use the login delay command for authentication attempts.
Use the none keyword when configuring the authentication method list.
Use the aaa local authentication attempts max-fail global configuration mode command with a higher number of acceptable failures.
Use the login local command for authenticating user access.
the switch that is controlling network access
the client that is requesting authentication
the router that is serving as the default gateway
the authentication server that is performing client authentication
password encryption
separate authentication and authorization processes
802.1X support
SIP support
utilization of transport layer protocols
The authorization feature enhances network performance.
User access is restricted to certain services.
A user must be identified before network access is granted.
User actions are recorded for use in audits and troubleshooting events.
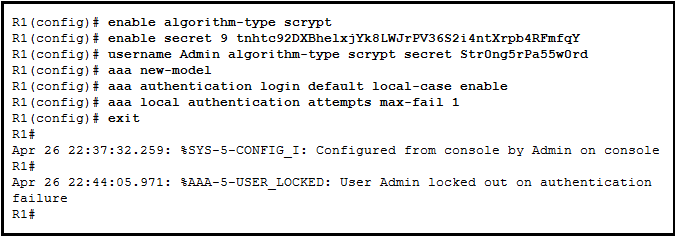
The locked-out user stays locked out until the clear aaa local user lockout username Admin command is issued.
The locked-out user failed authentication.
The locked-out user stays locked out until the interface is shut down then re-enabled.
The locked-out user should have used the username admin and password Str0ngPa55w0rd.
The locked-out user is locked out for 10 minutes by default.
true
false
The router outputs accounting data for all outbound connections such as SSH and Telnet.
The router collects and reports usage data related to network-related service requests.
The router provides data for only internal service requests.
The router outputs accounting data for all EXEC shell sessions.
local AAA
server-based AAA over TACACS+
server-based AAA
local AAA over TACACS+
local AAA over RADIUS
server-based AAA over RADIUS
Use the show aaa user command.
Use the show aaa local user lockout command .
Use the show aaa sessions command .
Use the show running-configuration command .
the supplicant
the authentication server
the switch that the client is connected to
the router that is serving as the default gateway
That’s all the latest CCNA Security chapter 3 exam questions and answers. Please share the new CCNA Security exam questions via the comment section.
Related Questions:
CCNA security chapter 3 exam answers 2018
CCNA security 2.0 hands-on skills exam
CCNA security chapter 3 exam answers
CCNA Security exam questions and answers pdf
CCNA security v2.0 exam answers
CCNA security final exam packet tracer
Which solution supports aaa for both radius and tacacs+ servers?
What is a characteristic of aaa accounting?
CCNA security final exam answers 2018
CCNA security netacad
